Compile Clamav For Mac
ClamAV on Mac with Kerio MailServer
- Compile Clamav For Mac Installer
- Compile Clamav For Mac Os
- Clamav Windows
- Compile Clamav For Mac High Sierra
Modclamav has so far been tested on Linux, Solaris and Mac OS X (the latter only in local mode on Jaguar, Clamav 0.70 on Panther finds a suitable pthreads implementation and compiles the daemon, and modclamav seems to work in daemon mode on Panter, but I have not fully tested it). If you succeed to install the module on some other platform. ClamAV Signatures. Anyone can learn to read and write ClamAV signatures. Take a look at the signature writing documentation and phishing signature writing documentation to get started! Installation Instructions UNIX Build from Source on Linux/Unix/Mac. For basic compile and install instructions on Linux/Unix platforms, check out the install. compiling on Panther and knew better than I how to resolve the issues. I wouldn't disagree with either of the assessments above, but I'm also quite sure that I've gotten more value from ClamAV than I've spent in terms of either time or money. ClamAV doesn't have to be perfect to still be quite useful, even if 0.88.x seems to be more.
Once you have done that, the easiest thing is to either use the Xcode IDE or use gcc, or nowadays better cc (the clang LLVM compiler), from the command line. According to Apple's site, the latest version of Xcode (3.2.1) only runs on Snow Leopard (10.6) so if you have an earlier version of OS X you will need to use an older version of Xcode.
© May 2019 Anthony LawrenceI downloaded ClamAV source from https://www.clamav.net. A simple ./configure; make; make install in the source directory was all that was required (thogh you do have to install the Xcode Tools from your install cd if you haven't already).
Well, gosh, that was easy. Now what?
Well, that depends on what you plan to do with it. If you only plan to scan files on your drives, there's nothing else you need.If you are planning to use the supplied 'clamav-milter' (see Sendmail Milters),you need to add the milter to your mail configuration (and you would have needed to run './configure --enable-milter' before compiling).See clamav-milter(link dead, sorry)for very basic instructions on adding this milter to sendmail.
In my case, I wanted to use it with Kerio Mailserver.
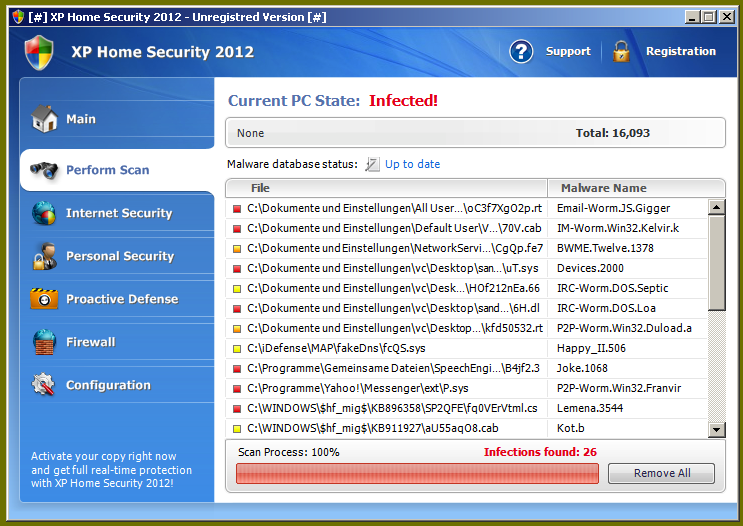
Kerio MailServer is able to work with several virus scanning engines. The preferred primary is McAfee, but (depending on your OS platform) other plugins can be used. As of version 6.1, they introduced the ability to do dual scanning, which allows each message to be scanned by two different AV products (one must be their McAfee option). Dual scanning can increase the chances of detecting viri.
Now with the 6.2 release (available in beta as I write this), ClamAV support has been added and can be used either as the stand-alone scanner or as the secondary to McAfee.
To use ClamAV with Kerio MailServer you need to get /usr/local/sbin/clamd running on the Mac (basically the same procedure applys to Linux) . That's going to requre editing (with sudo) two configuration files: /usr/local/etc/clamd.conf and /usr/local/etc/freshclam.conf
ClamAV forces you to at least comment out the 'Example' line from these files:
# Comment or remove the line below.
Example
For freshclam.conf that may be all you want or need to do, but at least this made you aware that the file exists and that you do have options to control freshclam. Freshclam is the program that updates Clamav's virus database, so you probably want to set it to run periodically with cron.
You'll need to do a little more with /usr/local/etc/clamd.conf. In addition to commenting out the 'Example', you need to set 'TCPSocket 3310' and you probably want to set 'TCPAddr 127.0.0.1' unless Kerio is running on a different machine than ClamAV.
With these set, you can start /usr/local/etc/clamd. After starting it, you should see it listening on port 3310:
$ sudo /usr/local/sbin/clamd
$ sudo lsof -i:3310
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
clamd 18975 root 0u IPv4 0x2f92e88 0t0 TCP localhost:dyna-access (LISTEN)
Of course you'll want clamd starting up on reboot. It would be best to handle that through Launchd but you could also just add it to /etc/rc if you want. Launchd gives you more control to restart if necessary.
Kerio automatically tests Clam with an EICAR file but you can send the same pattern to a local user if you aren't the trusting sort. I tested, and found the expected entry in the Kerio Security Log:
I'm glad to see this support added to Kerio. I think it would have been better if they had implemented milter support because that would allow even more options for Kerio users, but this is a welcome addition.
Got something to add? Send me email.
(OLDER) <- More Stuff -> (NEWER) (NEWEST)
Printer Friendly Version
-> -> ClamAV on Mac
Inexpensive and informative Apple related e-books:
El Capitan: A Take Control Crash Course
Take Control of Numbers
iOS 10: A Take Control Crash Course
Take Control of IOS 11
Photos: A Take Control Crash Course
Clam AntiVirus (ClamAV) is a free, cross-platform antivirus tool-kit able to detect many types of malicious software, including viruses. One of its main uses is on mailservers as a server-side email virus scanner. The application was developed for Unix and has third party versions available for AIX, BSD, HP-UX, LINUX, MAC OS X, openVMS, OSF (Tru64) and Solaris.Here in this section we will try to automate the entire Process of clamAv using cronjob.We are using Red-hat enterprises Linux platform to test this.
Step 1: Install ClamAV
We can use yum command to install clamav in the server.
# yum install clamav clamav-db clamd
Try to start the clamav by typing the command below.
# /etc/init.d/clamd start
This automatically sets up a daily cron job which runs fresh clam to update virus definitions.
Step 2 : Create new cron jobs to run daily virus scans
First we need to create a file clamscan_daily in cron.daily folder.It will help us to paste our script in this file,all the files or scripts in this folder will run automatically daily.
Create a clamscan_daily file in the folder cron.daily
#vi /etc/cron.daily/clamscan_daily
Paste the below script in the file and save.
#!/bin/bash
# email subject
SUBJECT=”VIRUS DETECTED ON `hostname`!!!”
# Email To ?
EMAIL=”alert@domain.com”
# Log location
LOG=/var/log/clamav/scan.log
check_scan () {
# Check the last set of results. If there are any “Infected” counts that aren’t zero, we have a problem.
Compile Clamav For Mac Installer
if [ `tail -n 12 ${LOG} | grep Infected | grep -v 0 | wc -l` != 0 ]
then
EMAILMESSAGE=`mktemp /tmp/virus-alert.XXXXX`
echo “To: ${EMAIL}” >> ${EMAILMESSAGE}
echo “From: alert@domain.com” >> ${EMAILMESSAGE}
echo “Subject: ${SUBJECT}” >> ${EMAILMESSAGE}
echo “Importance: High” >> ${EMAILMESSAGE}
echo “X-Priority: 1” >> ${EMAILMESSAGE}
Compile Clamav For Mac Os
echo “`tail -n 50 ${LOG}`” >> ${EMAILMESSAGE}
Clamav Windows
sendmail -t < ${EMAILMESSAGE}
fi
Compile Clamav For Mac High Sierra
}
clamscan -r / –exclude-dir=/sys/ –quiet –infected log=${LOG}
Step 3 : set-up proper permission to the file
#chmod +x /etc/cron.hourly/clamscan_hourly
This steps will help to setup automation of clamav in the server and reports are send directly to the email given in the script.
If you require help, contact SupportPRO Server Admin